The DoD’s Vision and the Public Sector’s Shoe-String Budget
By Robert Buccigrossi, TCG CTO

The government-wide push for Zero Trust is a mandate intended to minimize the impact of service and system vulnerabilities. At a recent ATARC webinar, leaders from across the Department of Defense (DoD) outlined a comprehensive, well-funded vision for this security paradigm. Their findings are valid and represent a necessary evolution in defending the nation’s most critical systems.
However, for many civilian agencies and the contractors who support them, this vision is mostly an “unfunded mandate”: a sweeping requirement with no new budget to match. This creates a tale of two mandates: the ideal and the achievable.
Part 1: The DoD’s Vision — A Blueprint for a Secured Future
The DoD’s approach to Zero Trust is a heavy engineering lift, designed to re-architect its entire information enterprise from the ground up. The lessons from their experience provide a valuable blueprint for what a fully-realized Zero Trust architecture looks like.
Lesson 1: Governance is a Heavy Engineering Lift, Not a Policy Paper
For the DoD, the first step isn’t policy—it’s a massive network consolidation project. The Army’s effort to unify its dozen-plus disparate networks under the Army’s Unified Network Plan (AUNP) highlights a core truth: you cannot govern what you don’t control. This multi-year infrastructure overhaul is the foundational work required to apply consistent Zero Trust principles at an enterprise scale.
Lesson 2: Identity is the New Perimeter (But Don’t Tear Down the Fences)
The DoD’s strategy, grounded in NIST Special Publication 800–207, treats identity as the new perimeter. This means supplementing traditional North-South (in/out) traffic controls with robust East-West (internal) controls. The goal is to contain an attacker’s blast radius by requiring authentication and authorization for every interaction between internal applications and services, not just at the network edge.
Lesson 3: Automation is the Only Way to Survive Compliance
The DoD recognizes that the “paper route” for compliance is unsustainable. Their strategy embraces automation to achieve the continuous verification that Zero Trust demands. This is being implemented with the Open Security Controls Assessment Language (OSCAL), a machine-readable framework that turns compliance from a manual documentation task into an automated data pipeline, making a continuous ATO (cATO) possible.
Lesson 4: AI Models Are the New Crown Jewels—Protect Them Accordingly
Looking ahead, the DoD views the AI models being integrated into its systems as high-value targets. Securing AI is not just about the infrastructure it runs on but protecting the models themselves from adversarial attacks like data poisoning or evasion. This forward-looking stance is already being backed by guidance from both NIST and the DoD CIO’s office, treating AI as a “crown jewel” that must be secured by design.
Part 2: The Reality — An Iterative Path for the Unfunded Mandate
The DoD’s approach is comprehensive and correct for its mission. For civilian agencies with limited modernization budgets, however, a different strategy is needed. At TCG, we recommend an iterative implementation based on two key principles: prioritizing the biggest security gaps and leveraging the technologies you already have on hand.
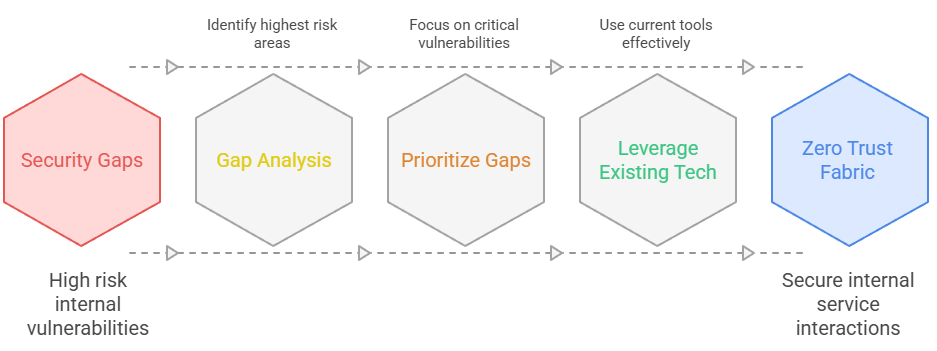
The goal of Zero Trust is to stop attackers from “leap-frogging” between services on your internal network. You achieve this by enforcing verifiable authentication and authorization for every interaction.
Suggestion 1: Start with a Gap Analysis, Not a Shopping List.
Before buying any new products, perform a gap analysis to find the areas of highest risk. Where are your components interacting with insufficient authentication? The most critical gaps are often not at the network edge, but deep inside your environment: a legacy application that trusts any connection from the local LAN, or a database that allows broad access to internal services. Prioritize these gaps and tackle the most critical one first. This iterative approach ensures that your limited resources are always focused on the most significant vulnerability.
Suggestion 2: Use Your Existing Toolkit to Enforce Trust.
You don’t need a brand-new platform to implement Zero Trust; you can use the “nearest-neighbor” technologies you likely already have. Most agency components already support the necessary standards. Focus on configuring and enforcing them:
- For Authentication & Authorization: Use your existing LDAP or Active Directory to manage credentials and access rights consistently.
- For Service-to-Service Security: Implement mutual TLS (mTLS) to ensure both the client and server are verified before any communication.
- For User & Client Authentication: Leverage OIDC/OAuth 2.0 and JWTs to manage secure, repeatable authentication across different services without exposing credentials.
By focusing on these technologies—which are often already licensed and in place—you can build a robust Zero Trust fabric without a massive capital investment.
Suggestion 3: Automate Compliance to Free Up Your Engineers.
Your most valuable resource is your engineering team’s time. Free them from the crushing workload of ATO documentation by automating compliance with OSCAL. By treating compliance as code, you convert wasted hours back into productive engineering time that can be used to close the gaps you identified in Suggestion 1.
This is why TCG, on behalf of OMB, developed the open-source AI workflow prototype, OPAL-AI. It analyzes software and documentation to automate evidence gathering for NIST SP 800–53 controls, using the OSCAL standards to streamline the process and give time back to engineers.
Suggestion 4: Apply the “Gap Analysis” Mindset to Emerging Threats like AI.
The most immediate AI risk isn’t a complex nation-state attack; it’s a data leakage “gap” created by employees using public LLMs. This is a high-priority vulnerability that can be closed with existing tools. A combination of clear policy, user education, and simple DNS or proxy blocks for unapproved AI sites addresses the most likely threat with minimal cost, allowing you to focus your budget on more complex architectural challenges.
Conclusion: From Vision to Value
Ultimately, the Department of Defense’s approach to Zero Trust is excellent, providing a comprehensive and strategically sound vision for the future of government cybersecurity. It serves as an invaluable north star for what a fully resourced, enterprise-wide implementation can achieve. This approach, however, is based upon the significant investment that the DoD is able to bring to bear.
For public sector agencies facing the reality of an unfunded mandate, the path forward must be different, but no less effective. The key is to recognize that Zero Trust is not a monolithic product to be purchased, but a set of principles to be applied. By adopting an iterative mindset, agencies can achieve a robust security posture on a “shoe-string” budget.